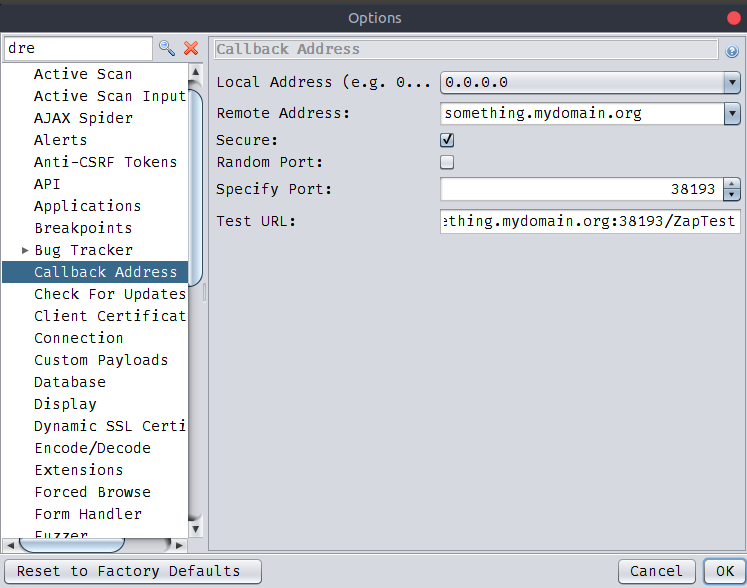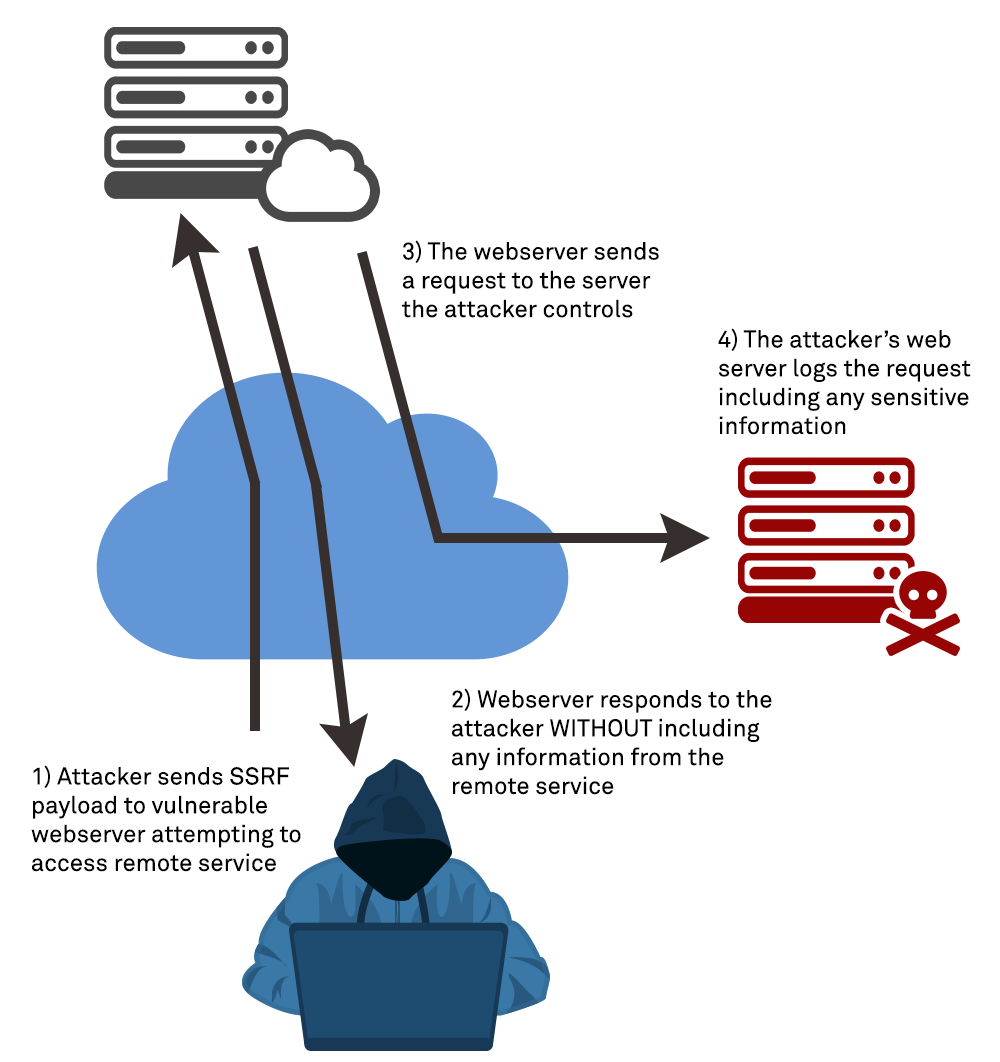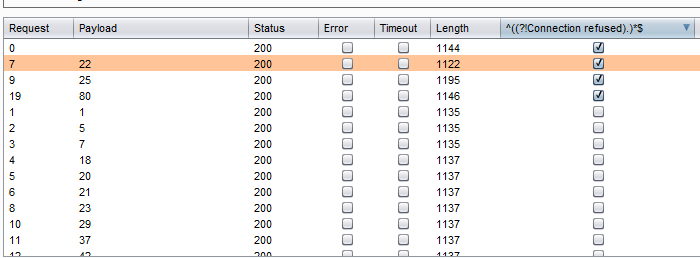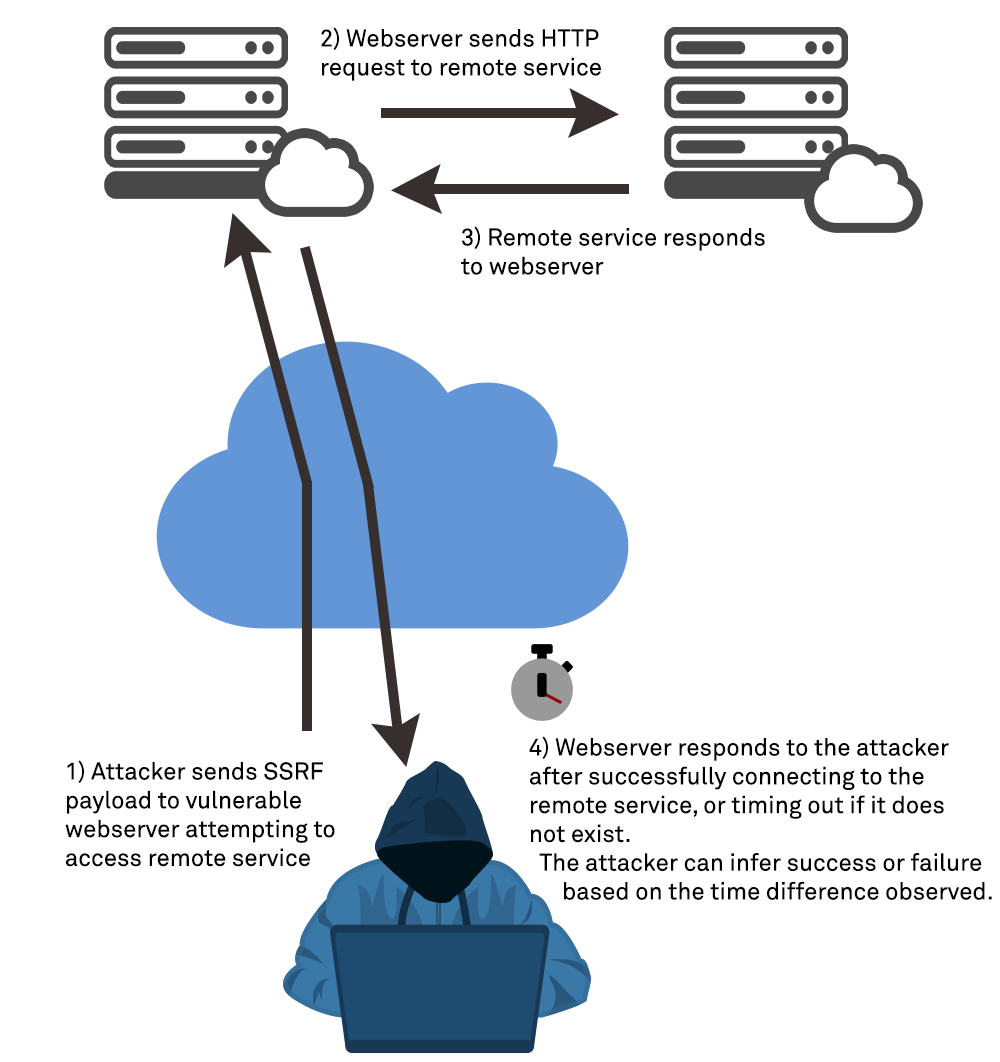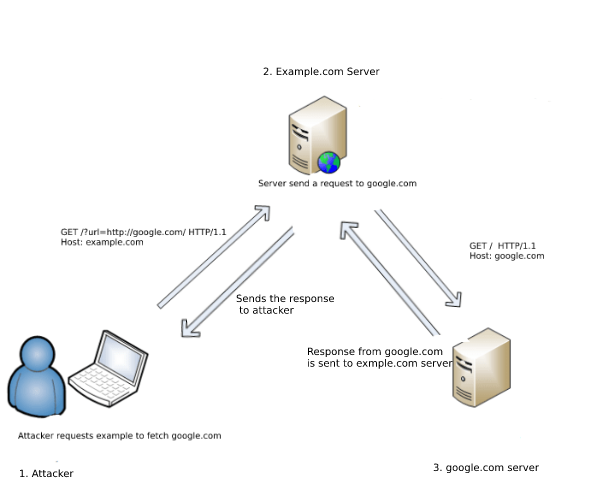
Invisible Attacker — Scanning Pattern Analysis Over Web Application | by Cybergladiatorasia | Medium

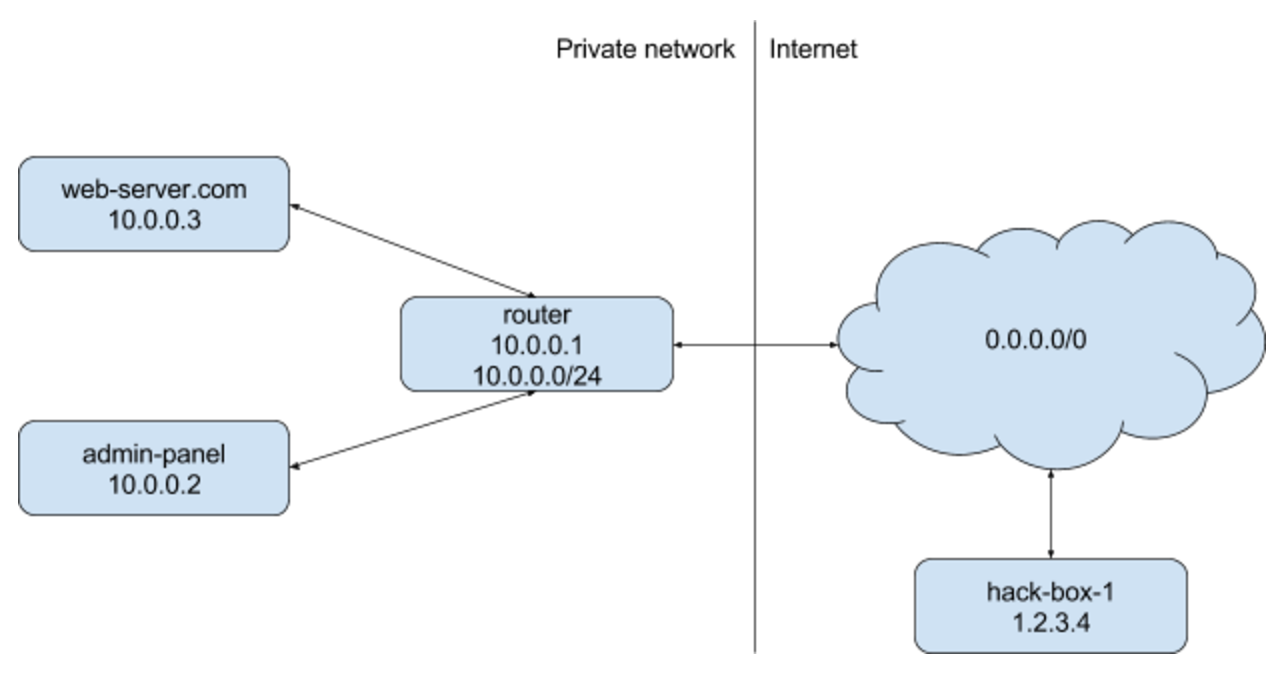
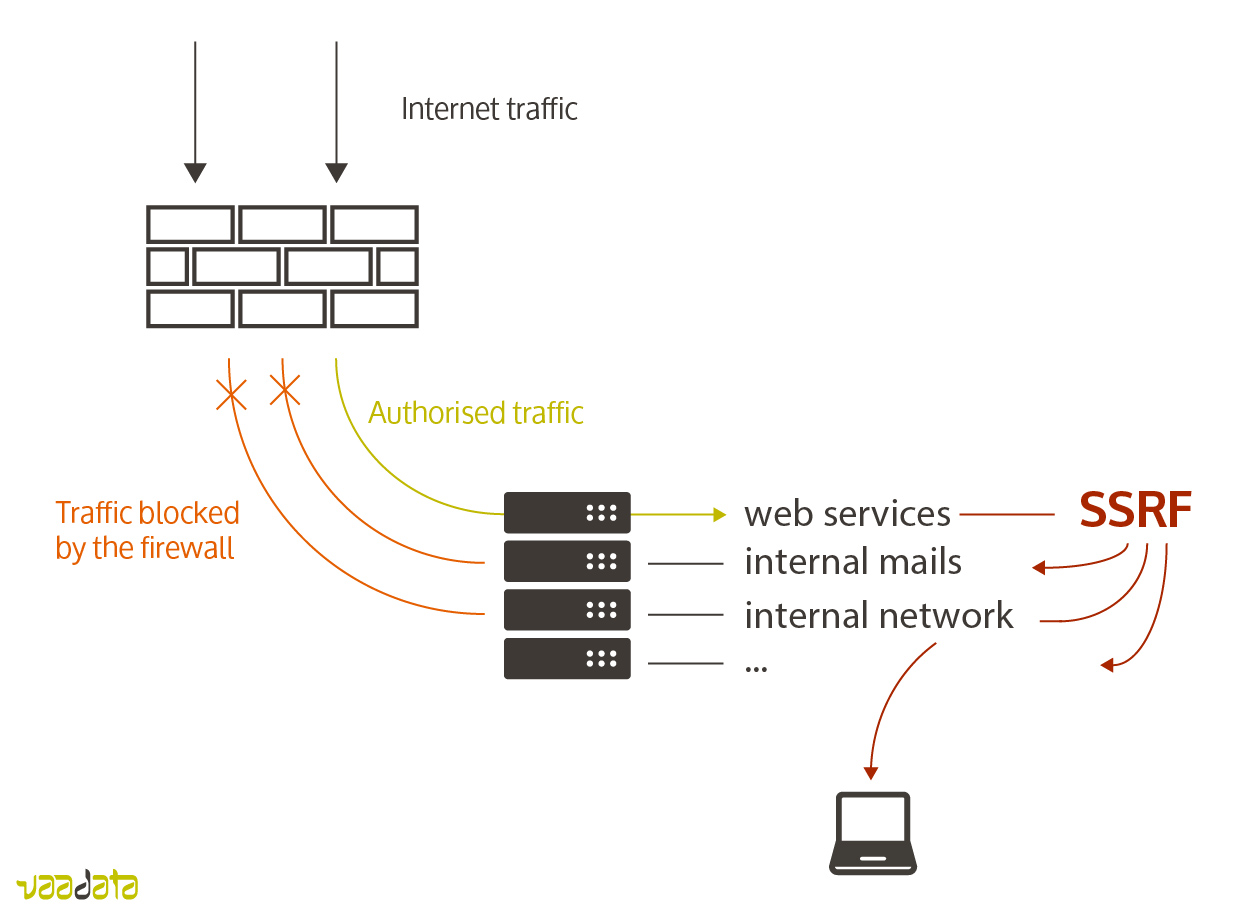
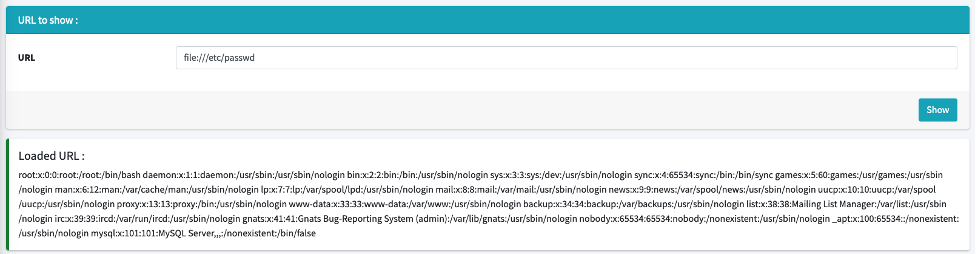
Beginner Guide To Exploit Server Side Request Forgery (SSRF) Vulnerability | by Muh. Fani Akbar | InfoSec Write-ups
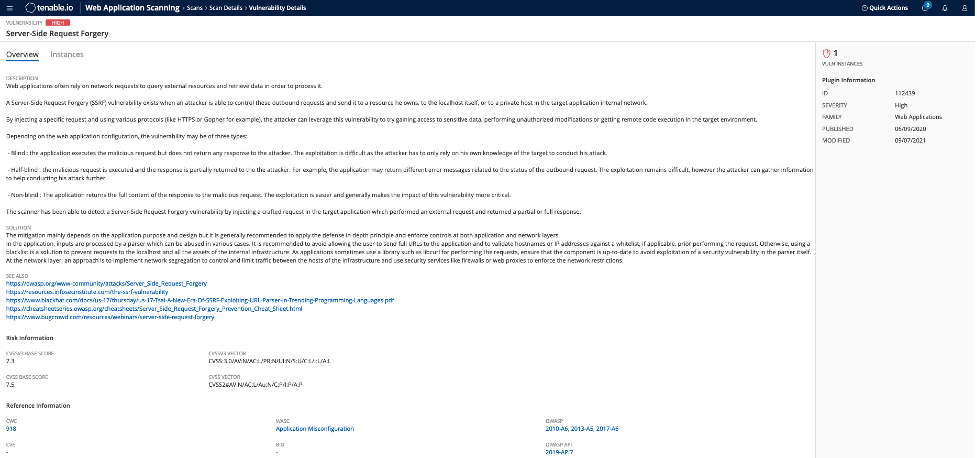
Identifying Server Side Request Forgery: How Tenable.io Web Application Scanning Can Help - Blog | Tenable®