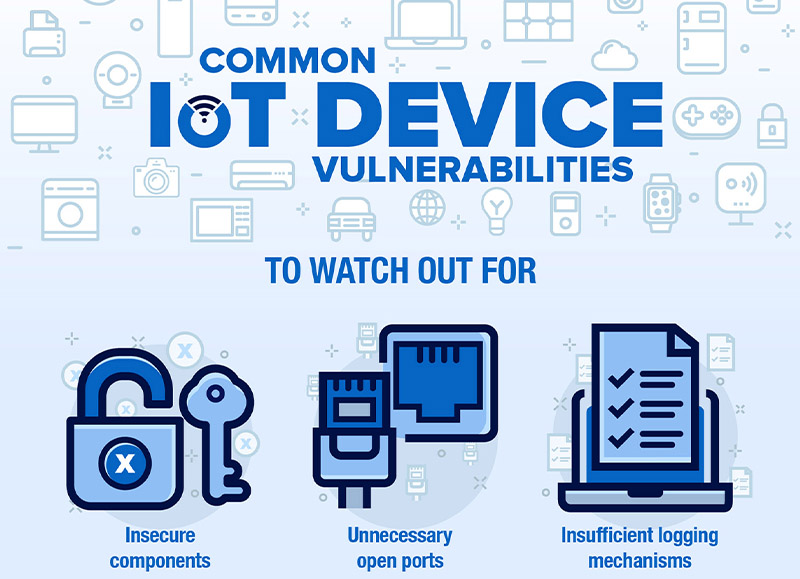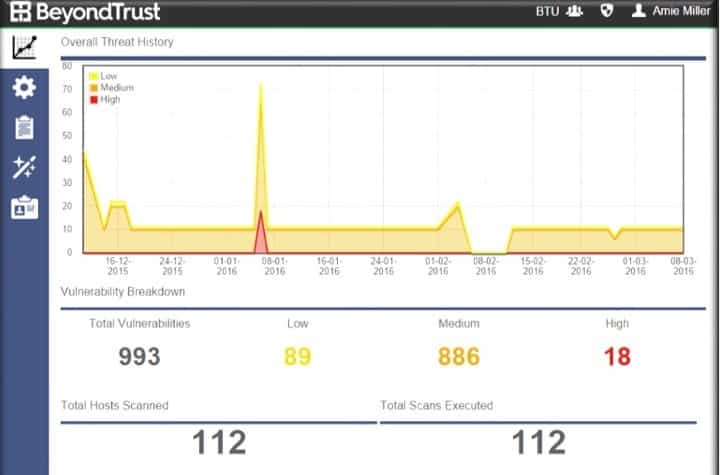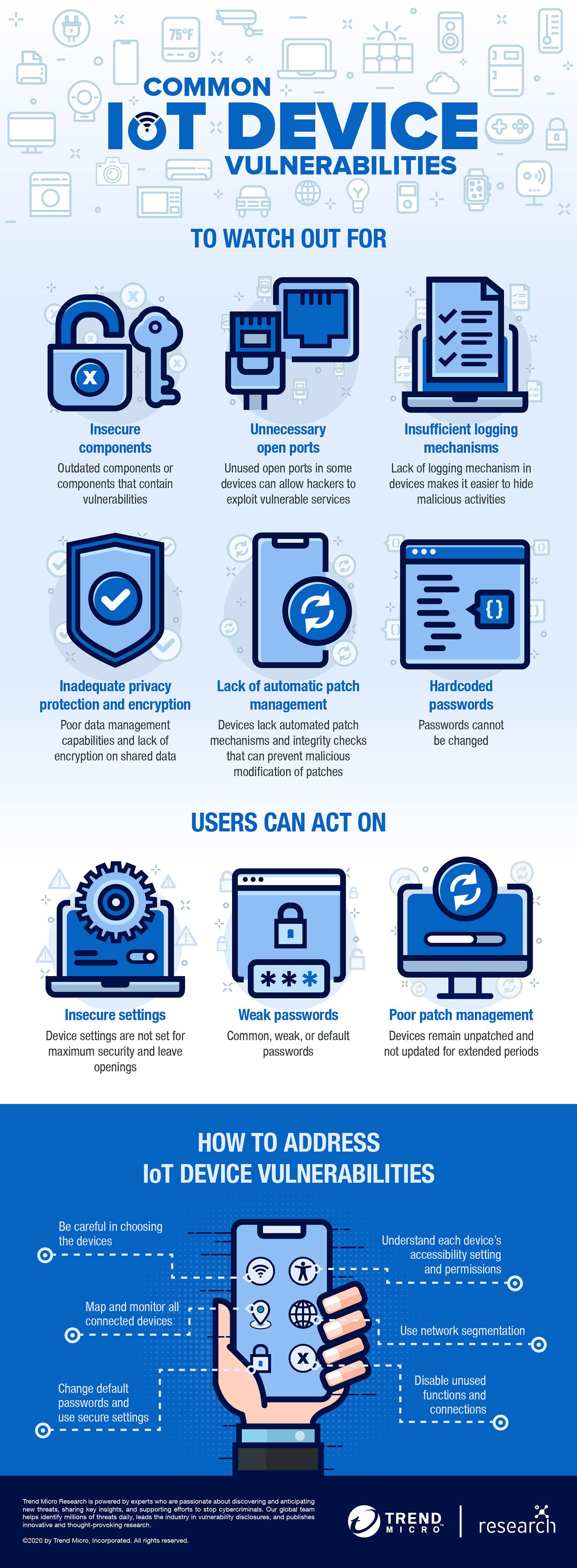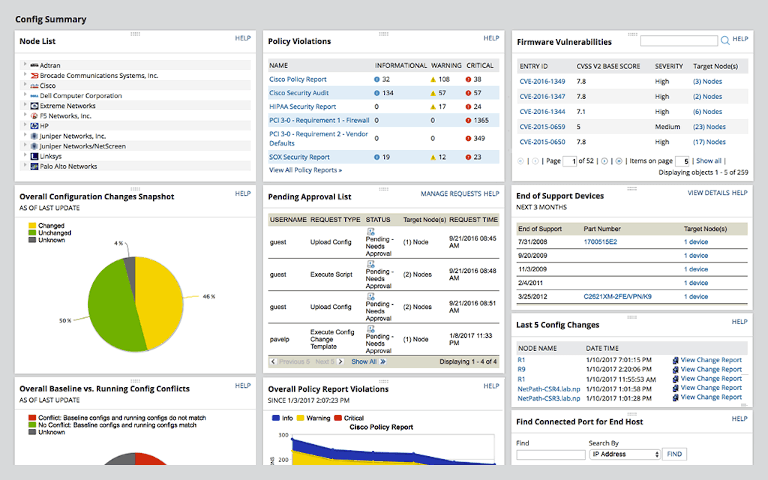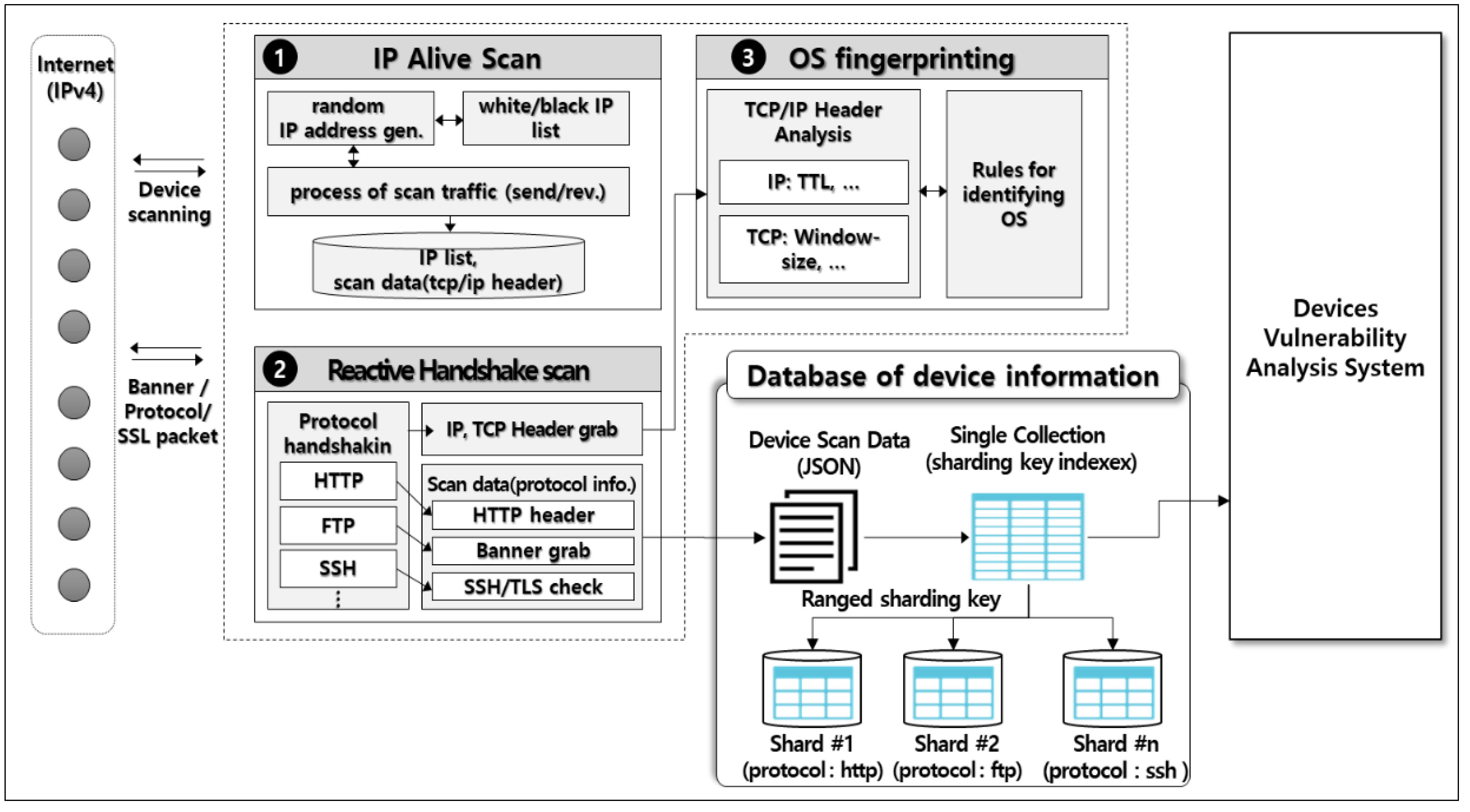
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices | HTML
GitHub - billy-osullivan/IOT-Protect-Continous-Vulnerability-Scanner: A continous vulnerability scanner which scanys for Qbot and Mirai vulnerabilites and displays results in a browser

Vulnerability Scanning System Used in the Internet of Things for Intelligent Devices | Semantic Scholar
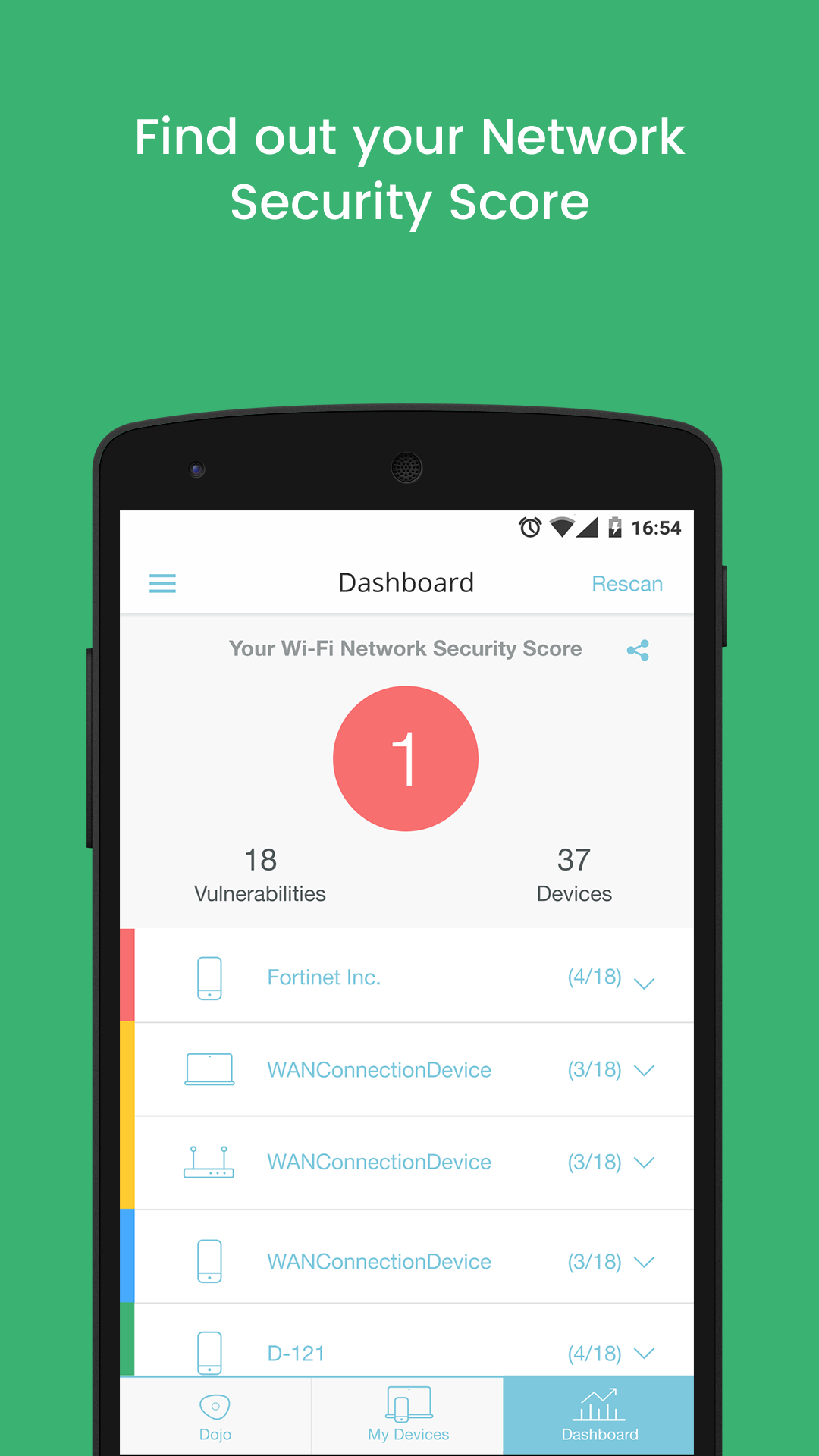
New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes

New Dojo Intelligent IoT Vulnerability Scanner App Provides Consumers With Deep Insight Into The Cybersecurity Risks In Their Smart Homes

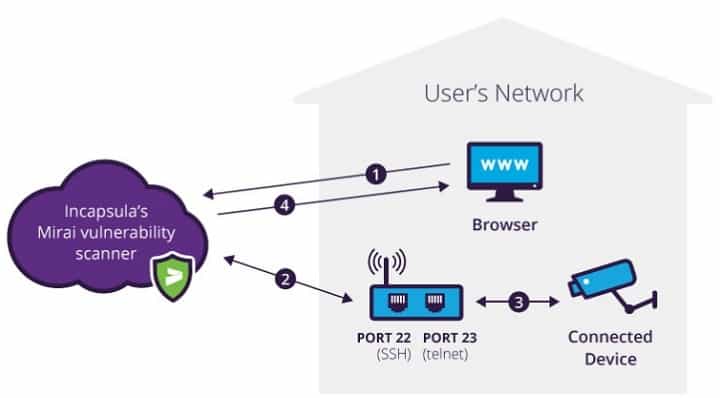
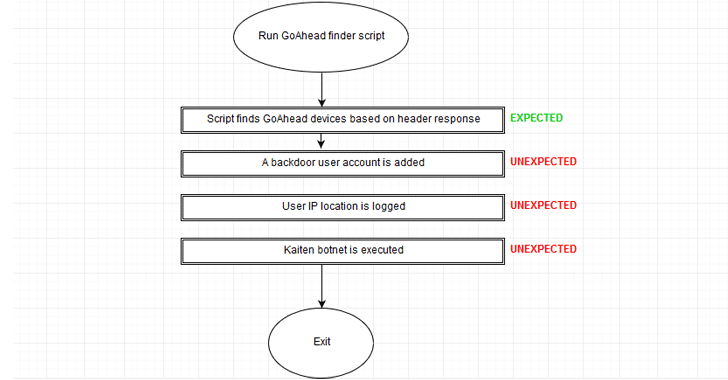





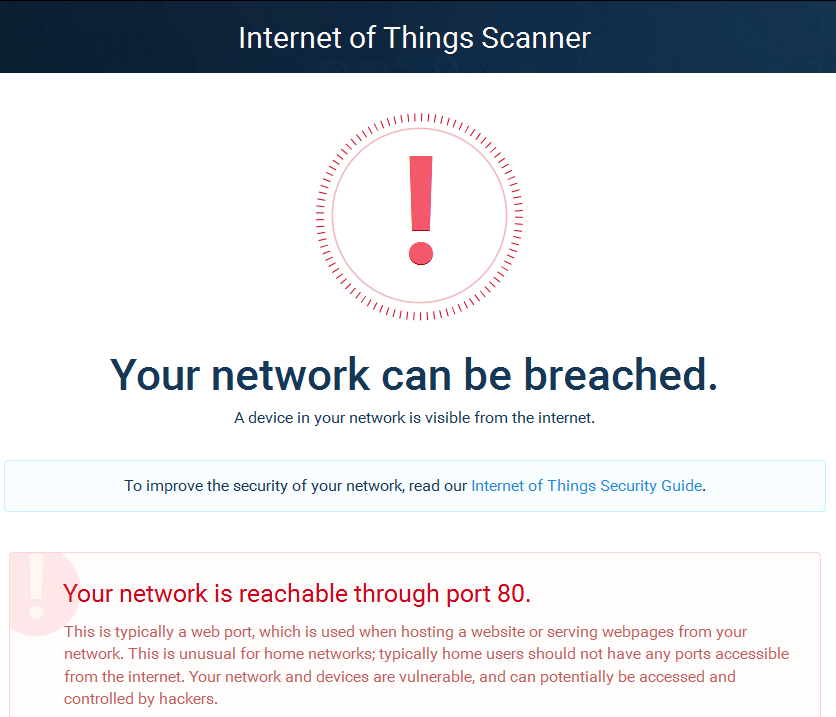


![Top 5 IoT vulnerability exploits in the smart home [list] Top 5 IoT vulnerability exploits in the smart home [list]](https://www.minim.com/hubfs/iot-vulns-feature-12.jpg)