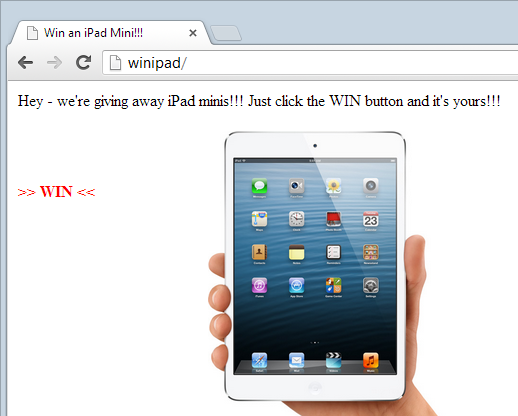
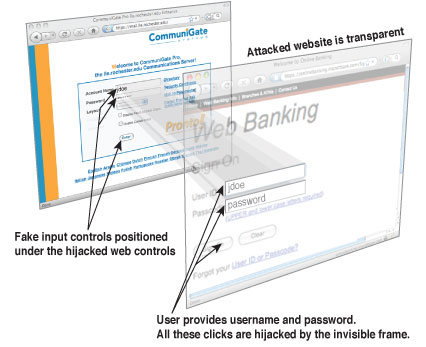
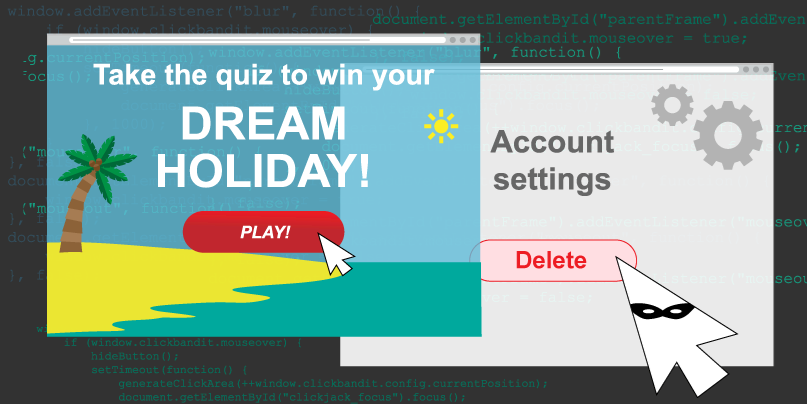
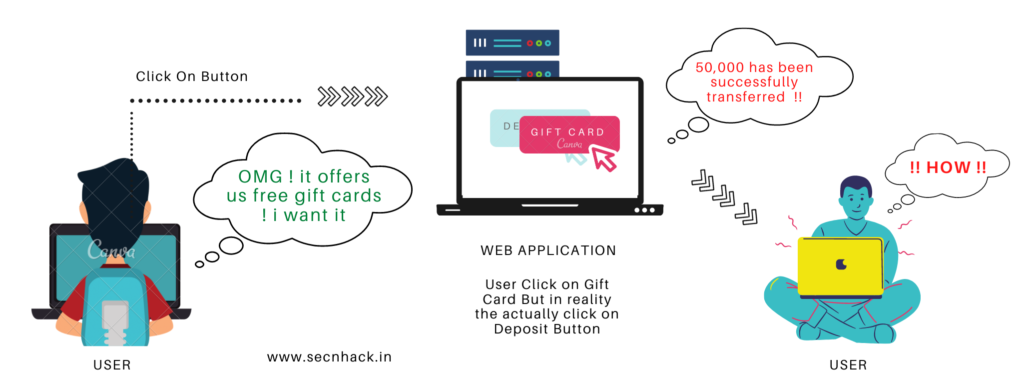
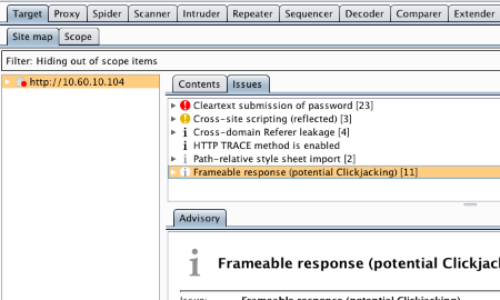
NMAS Click Jack Security Vulnerability: X-Frame-Options or the Content-Security-Policy's frame ancestor option missing to prevent Click Jacking attacks
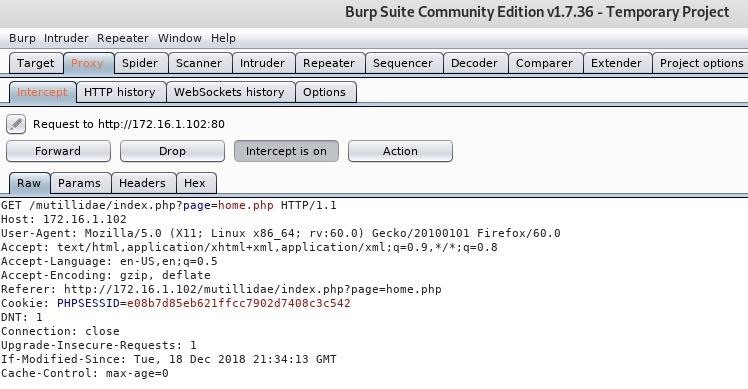
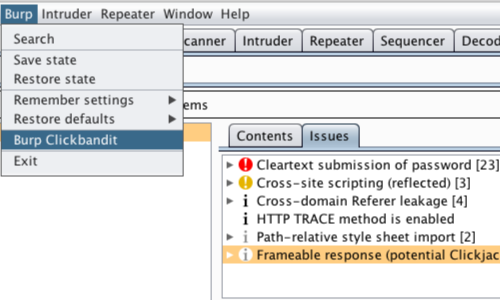
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo