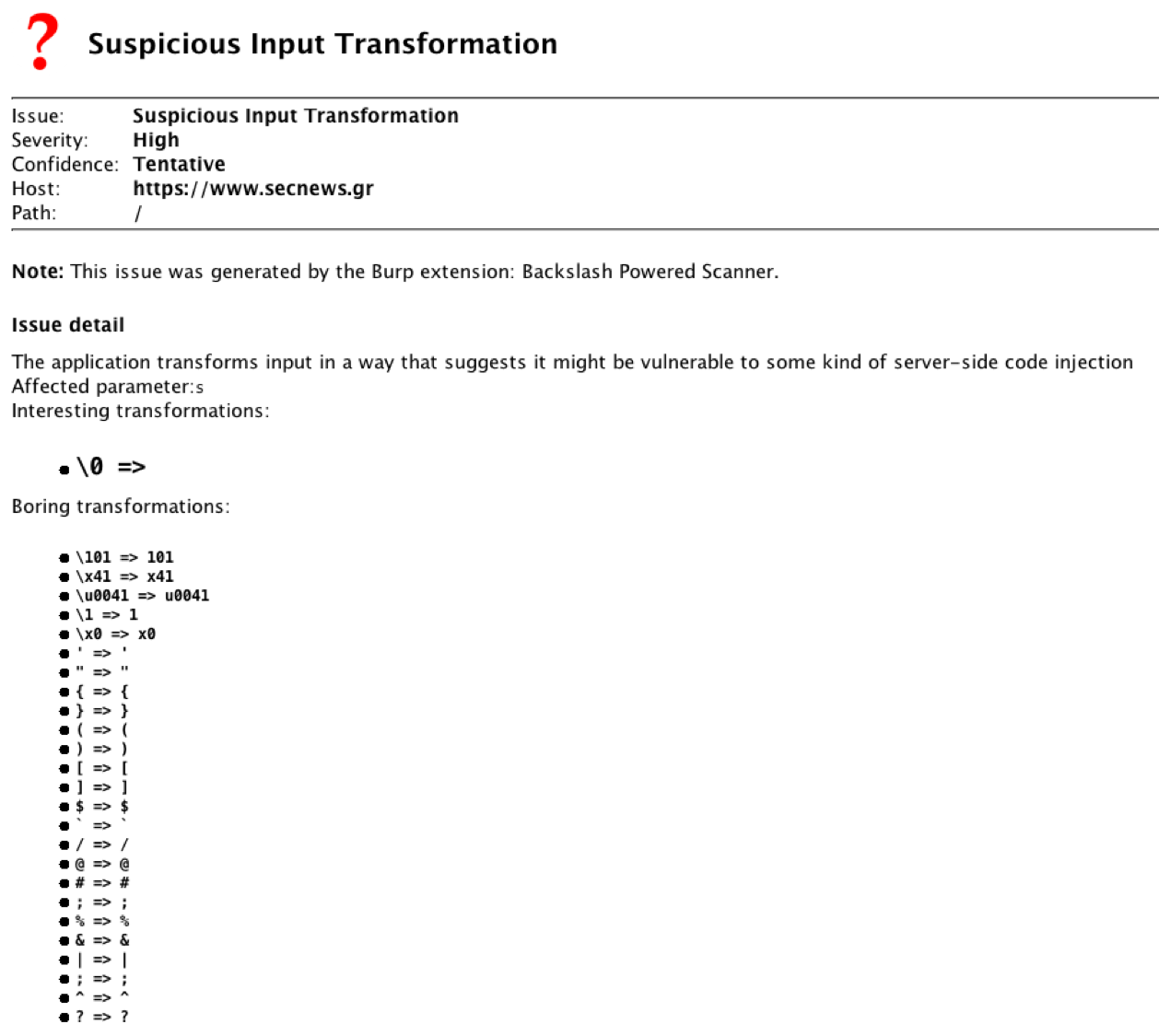
James Kettle on Twitter: "Backslash Powered Scanner can now detect proxy subfolder escapes using @orange_8361's path normalization research from last year - just enable 'experimental folder attacks'. https://t.co/Lxeb2qW1LP" / Twitter
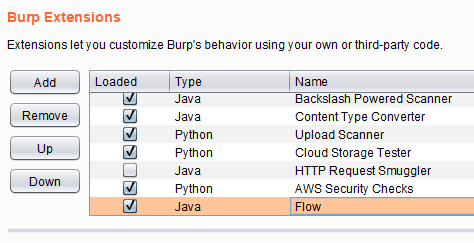
False positives/bad higlighting scanning REST url paths · Issue #2 · PortSwigger/backslash-powered-scanner · GitHub

James Kettle on Twitter: "Backslash Powered Scanner now uses the 'COM1' Windows reserved filename to identify if your input is being used in a file path on a backend. Also, you can

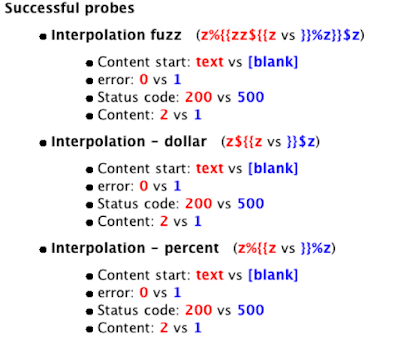
Finding High-Risk Web Vulnerabilities with a Small Number of Generic Payloads Detecting Server-Side Injection Vulnerabilities using Expression Probing. - ppt download

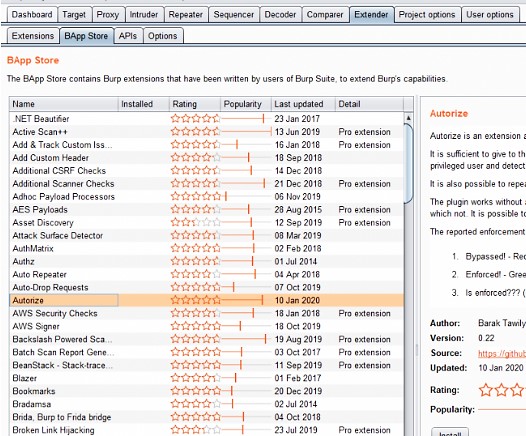
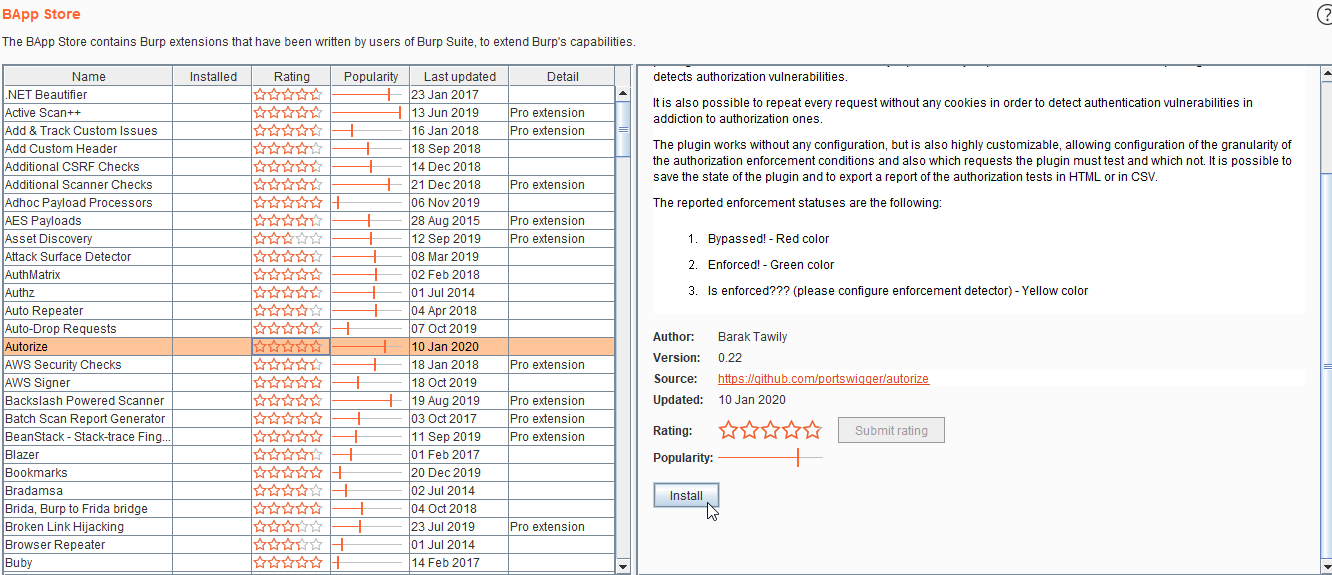
Nullwatch - Backslash Powered Scanning: Hunting Unknown Vulnerability Classes http://blog.portswigger.net/2016/11/backslash-powered-scanning-hunting.html?m=1 | Facebook